
How to containerize a Node.js Application
9 January 2017
Life of BluePi: 4 years of growth and how!
24 January 2017

Published by
BluePi
Data-Driven Business Transformation
Thinking to automate AMI backups; Use AWS Lambda, with ELB tags
If you’ve been following our blog, you would know how we love to talk about advances in technology and ensure that our readers get the most out of reading our posts. This is the thing about being a tech enthusiast, we start to believe in what sufficiently advanced technology can do; it becomes indistinguishable from magic. Technology feeds on technology, technology makes technology possible. Without much ado, let me put forth another informative piece, to help you get sorted with automating AMI backups and cleanup. In our earlier post, we discussed a key limitation when it comes to working with EC2 tags:
“The process works very well for all standalone instances unless the instance terminates. In cases where you might have a load balancer serving many instances, the tag attached to one instance may terminate for some reason, therefore, not creating the AMI. However, there’s a workaround using ELBs. It fetches all the load balancers with pre-defined tags (Backup for example), puts them in an array and passes them through a loop, before picking one instance attached to it, to create the AMI.”
Now going forward, in this blog-post, let us take you through the steps involved in automating the AMI backups and cleanups using AWS Lambda for ELB tags.
The process generally comprises of the following steps:
- Setup IAM Permissions
- Create Lambda Backup Function
- Create Lambda Cleanup Function
- Schedule Functions
- Tagging Elastic Load Balancer (ELB)
Side Note: Above steps are quite similar to the previous blog but here we are focusing on the functionalities for ELB tags.
1. SETUP IAM PERMISSIONS
Login to your AWS Management console, Go to Services, and click on IAM under Security & Identity.
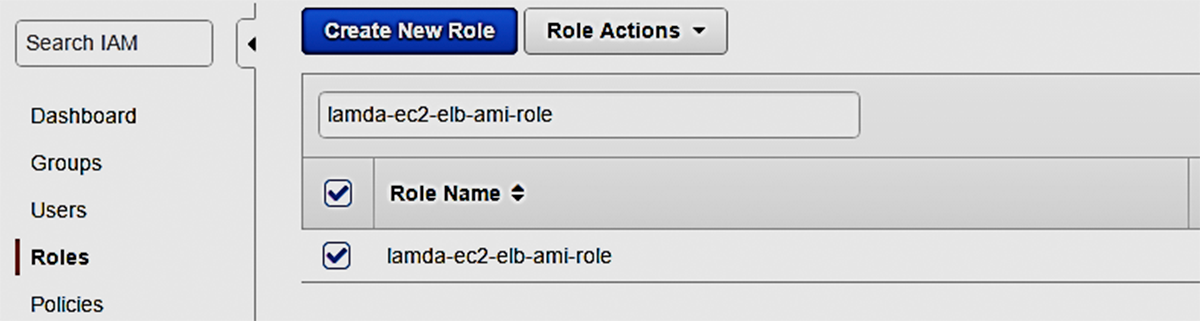
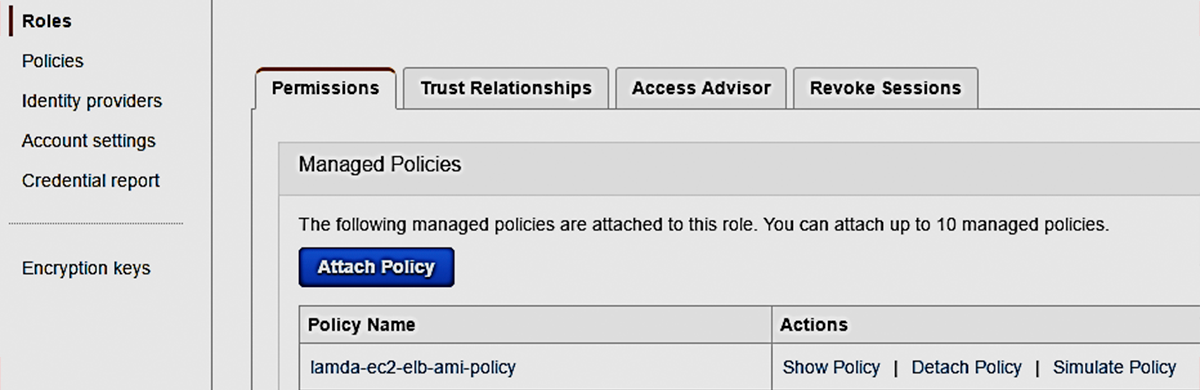
In IAM Dashboard, Click on Roles, and Create New Role with the R ole Name: lamda-ec2-elb-ami-role; Select Role Type in AWS Service Roles as AWS Lambda then proceed to create a role. Go to Policies tab; click Create Policy and select Create your own policy (you can name the policy as lamda-ec2-elb-ami-policy). Paste the content (additional permission to ELB) of the following JSON in Policy Document, and click on Create Policy.
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Action”: [
“logs:*”
],
“Resource”: “arn:aws:logs:*:*:*”
},
{
“Effect”: “Allow”,
“Action”: “ec2:*”,
“Resource”: “*”
},
{
“Effect”: “Allow”,
“Action”: “elb:*”,
“Resource”: “*”
}
]
}
Select the created policy, click on Policy Actions and Attach to select the role already created – lamda-ec2-elb-ami-role and click on **Attach Policy. **We have just created a role for which we have allowed permissions to ELB, EC2 instances and view logs in Cloudwatch:
2. CREATE LAMBDA BACKUP FUNCTION
Now that we have created a role and a policy, we’ll have to create the first function that allows us to backup by picking anyone instance from the attached (AWS) instances to ELB in our account, which has a “Backup” key tag. We don’t have to indicate a value here.
Here’s how the AMI backup script works:
- The script will first search for all the load balancer’s having a tag with “ Backup” on it.
- As soon as it has the load balancer’s list, it loops through each load balancer’s and fetch the instance ids for instances had been attached to the load balancer and put it in an array.
- Then pick the first index of instance id in an array list to create an AMI. Also, it will look for a “ Retention” tag key which will be used as a retention policy number in days. If there is no tag with that name, it will use a 7 days default value for each AMI.
- After creating the AMI it creates a “ DeleteOn” tag on the AMI indicating when it will be deleted using the Retention value and another Lambda function.
So here’s how you can create your first function. Go to Services, Lambda, and click Create a Lambda Function:
Login to your AWS Management console, Go to Services, and click on Lambda under Compute.
- Click on Functions Menu on the left, and click on Create a Lambda Function
- Select Blank Function and proceed with lambda
- Give a name for it - lambdaAMIbackups
- Select Python 2.7 as a Runtime option.
- You’ll have to write a code next by considering the above mentioned points.
- Select the previously created IAM role ( lamda-ec2-elb-ami-role) Click Next and Create Function.
2. CREATE LAMBDA BACKUP FUNCTION
Now that we have created a role and a policy, we’ll have to create the first function that allows us to backup by picking anyone instance from the attached (AWS) instances to ELB in our account, which has a “Backup” key tag. We don’t have to indicate a value here.
Also, it will look for a “ Retention” tag key which will be used as a retention policy number in days. If there is no tag with that name, it will use a 7 days default value for each AMI.
- After creating the AMI it creates a “ DeleteOn” tag on the AMI indicating when it will be deleted using the Retention value and another Lambda function.
So here’s how you can create your first function. Go to Services, Lambda, and click Create a Lambda Function:
Login to your AWS Management console, Go to Services, and click on Lambda under Compute.
- Click on Functions Menu on the left, and click on Create a Lambda Function
- Select Blank Function and proceed with lambda
- Give a name for it - lambdaAMIbackups
- Select Python 2.7 as a Runtime option.
- You’ll have to write a code next by considering the above mentioned points.
- Select the previously created IAM role ( lamda-ec2-elb-ami-role) Click Next and Create Function.


































